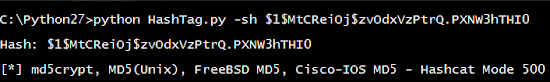
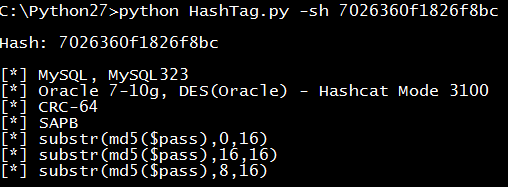
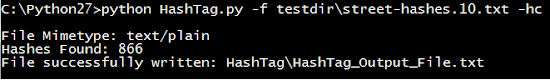
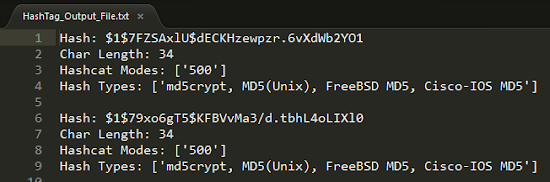
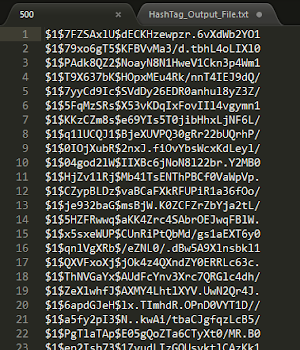
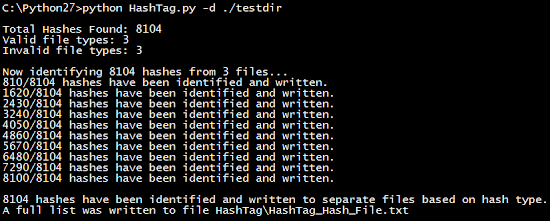
At first we must have 2 things:
1) Victim
2) Link for the websites, which i will tell you later
3) Email address [optional]
Let's start:
1. Find a victim, it can be anyone. I'll choose myself just to show you.
2. Open http://iplogger.org/ OR http://www.whatstheirip.com/ ( I prefer iplogger, because you don't need an email address )
3. So after you opened iplogger website, click on "Generate an invisible IPLOGGER" button. It should look like this


4. Then you will see a page, with some links. We want to send a link to someone, so we have to choose "Link to the untagged invisible picture" which is http://iplogger.org/1suf3.jpg for me.


5. After you copied the link, send it to anyone you want to get their ip.
6. Next click on button View Log, where will be your IPLOGGER ID written.
If there is nothing in log columns, nobody clicked the link yet. But as i told you before, i will click on it by myself.
As you can see, there is Date, Time, my IP address, country, region, city.


You can refresh the page with refresh button as much as you want. You can also reset the recent logs and you can save output to file, where will be date and ip address.
If you are trying to use http://www.whatstheirip.com/ site, you will have to put there your email address. Then you will have to click on "Get Link" and then copy a link you choose. I prefer bvog link, because it'll show
Not Found
The requested URL was not found on this server.


After you click on that link, you will get an email, which will be probably in spam folder.
The email will look like this:


Okey guys, it's all for this tutorial, hope you enjoyed it and hope some of you will find it useful.
1) Victim
2) Link for the websites, which i will tell you later
3) Email address [optional]
Let's start:
1. Find a victim, it can be anyone. I'll choose myself just to show you.
2. Open http://iplogger.org/ OR http://www.whatstheirip.com/ ( I prefer iplogger, because you don't need an email address )
3. So after you opened iplogger website, click on "Generate an invisible IPLOGGER" button. It should look like this


4. Then you will see a page, with some links. We want to send a link to someone, so we have to choose "Link to the untagged invisible picture" which is http://iplogger.org/1suf3.jpg for me.


5. After you copied the link, send it to anyone you want to get their ip.
6. Next click on button View Log, where will be your IPLOGGER ID written.
If there is nothing in log columns, nobody clicked the link yet. But as i told you before, i will click on it by myself.
As you can see, there is Date, Time, my IP address, country, region, city.


You can refresh the page with refresh button as much as you want. You can also reset the recent logs and you can save output to file, where will be date and ip address.
If you are trying to use http://www.whatstheirip.com/ site, you will have to put there your email address. Then you will have to click on "Get Link" and then copy a link you choose. I prefer bvog link, because it'll show
Not Found
The requested URL was not found on this server.


After you click on that link, you will get an email, which will be probably in spam folder.
The email will look like this:


Okey guys, it's all for this tutorial, hope you enjoyed it and hope some of you will find it useful.