|
|
Recently I was at home, playing with my BSNL router. For those who
don't know what BSNL is, its the AT & T of India, known for very bad
customer support :) |
|
|
|
|
|
|
|
In this article, I will walk you through step by step illustrations
on how to hack into your local router and explore it inside out.
Though I am using my BSNL router here but steps and method will be
similar for your modem/router as well. |
|
|
|
|
|
|
|
| BSNL router is manufactured by SemIndia and distributed by ITI. It
follows the tracks of using firmware of different routers (Broadcom to
be specific, BCM6338 stands for Broadcom router firmware version 96338,
deployed in US robotics ones and some other popular routers). Mine is
DNA-A211-1, one of most popular ones in India. |
| |
| |
| |
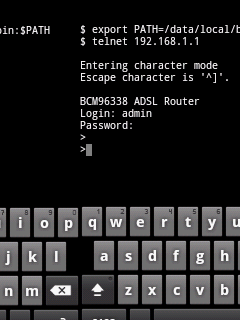
| To start with, I telnet into my router with my credentials and I am
greeted with welcome screen as shown in screen below, |
| |
 |
| |
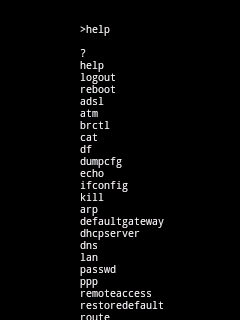
| Once you are in, first step will be to figure out what are the
services it has to offer, so I typed the usual 'help' and found
following commands. |
| |
 |
| |
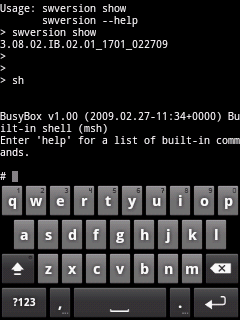
| I started with basic command, "swversion" to get the version. Then
with some hunting, I came to know that "sh" command runs over my router,
ran it and voila, familiar interface of busybox snaps in. |
| |
 |
| |
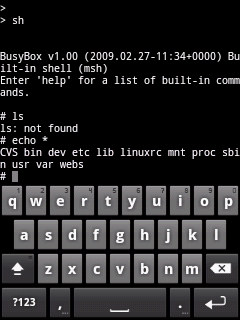
Great, now thats worth something. For those who don't know hat
busybox is, its a multicall binary. My android has it too. Seeing the
version made me tick, it was running an older version of busybox.
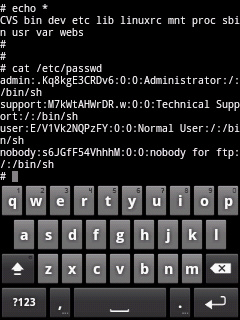
Then I tried ls command, but it didn't work, hence tried "echo
*" and it showed up everything as seen below |
| |
 |
| |
| Next comes the magic command "cat /etc/passwd" and there we go
again. |
| |
 |
| |
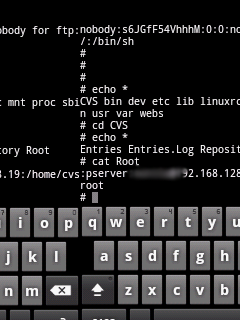
| After that, I went on exploring other directories. Got into CVS and
found information regarding CVS and pserver, note worthy one is the
credentials of pserver. |
| |
| pserver:xyzabc@192.168.128.19:/home/cvsroot |
| |
Not much of an interest though as they are of a private LAN. On
googling, I found out that account belonged to XYZ (name changed for
privacy), employee at
SIEMIndia.
Next, I moved on to /etc directory, |
| |
 |
| |
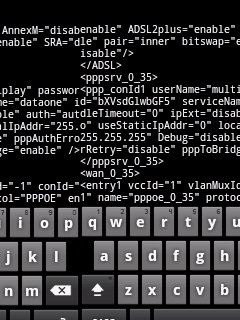
| lots of directories here, as a rule of thumb I opened default.cfg |
| |
 |
| |
| Generic stuff, but what caught my eye was this line, |
| |
| ppp_conId1 userName="multiplay"
password="kIMa1bXVsdGlwbGF51AG" |
| |
This might come in handy (use your creativity :)).
But
then I thought that why not to access the router from web interface.
Logged in to it and then went to "management" and downloaded the
backupsettings.conf file, |
| |
 |
| |
| On opening, it was like as shown below, |
| |
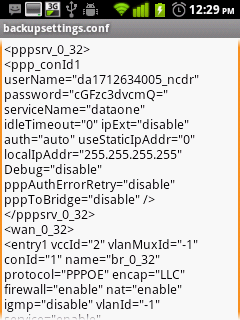 |
| |
I was not able to find the above credentials in it, hence I came to
a conclusion that they must be somewhat for internal purposes.
Moving on, I thought why not to try to create an arbitrary file .
Tried following command |
| |
| echo 'rishrockz' >> rdx |
| |
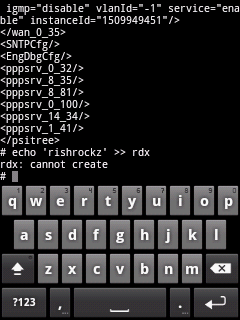 |
| |
But it failed. It was not easy to figure out the writable directory
as I was not able to determine the file permissions since this version
of busybox doesn't has ls or stat command.
Finally little bit of
exploring found that /var is writable. Tried creating a file again, it
succeeded ! |
| |
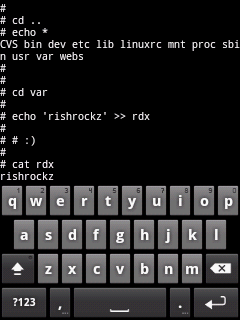 |
| |
Well, there is lot more to explore, this is just tip of iceberg!
Next time I am be thinking of going to compile programs
(http://people.debian.org/~debacle/cross/) and copying over them using
echo (once I get a PC), I have got some nice ideas and will be hacking
with them.
In the mean time, for those who are wondering
what this machine has, here is the bootup log. |
| |
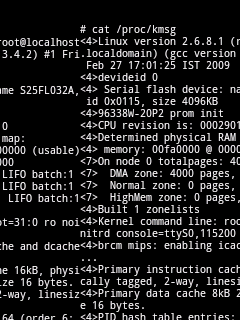 |
| |
| |
| :) enjoy it |
0 comments:
Post a Comment